Using the OpenPGP and AES Encryption
A mixed OpenPGP and AES encryption chain is applied to the media files stored on a USB drive:
| ● | The AES layer allows the encryption and decryption of media files. The AES keys are derived from a passphrase generated at every boot. |
| ● | The OpenPGP layer allows the encryption and decryption of the AES keys. The OpenPGP encryption standard is based on pairs of private and public keys. The two matching private and public keys revert each other actions. |
With the OpenPGP+AES encryption used in Picolo.net HD1, the protection mechanism works as follows:
| 1. | Each time the Picolo.net HD1 boots, it creates a new AES key (passphrase) and stores it in its volatile memory. |
| 2. | You upload the OpenPGP public key on the non-volatile memory of the Picolo.net HD1 device. |
| 3. | When the Picolo.net HD1 records media files and stores them on the USB drive, it secures them with the AES encryption. |
| 4. | The current AES passphrase, encrypted with the OpenPGP public key installed, is copied in a separate folder of the USB drive. |
| 5. | When users get the USB drive, they use the OpenPGP private key received to unseal the files. The appropriate AES keys are then automatically used to decrypt the media files. |
The software programs referred to in this section are solely intended to explain how to operate Picolo.net HD1.
We do not endorse these programs. Other programs complying to IETF RFC4880 allow you to perform the same tasks.
| 6. | Download and install Gpg4Win. |
| 7. | Click the New Key Pair button to enter the Key Pair Creation Wizard. |
| 8. | Enter the name and the e-mail address identifying the owner of the new keys |
| 9. | Click Advanced Settings and edit the following settings if requested: |
| □ | the certificate validity in the Valid until field |
| □ | the encryption algorithm in Key Material |
We tested the key pair generation with the default settings (RSA 2048 bits).
| 10. | When requested, enter twice the passphrase to be able to create the key. |
The passphrase is used only on your local computer to keep the private key safe on your disk.
| 11. | When the key pair is created, right-click on your key and select Export in the contextual menu. |
The software creates a new file with the public key.
The Picolo.net HD1 server preferably uses e-mail addresses to identify key owners.
You can identify a key without an associated e-mail address only through its hexadecimal signature.
| 12. | Check that you have gpg (GnuPG) package on your system. |
| 13. | If you already have a key pair, use the command gpg --list-keys to locate it. |
$ gpg --list-keys -------------------------------- pub 2048R/F2061AC8 2019-01-19 ^^^^^^^^---------------------------------------- the key ID we need. uid Picolo Developer <developer@picolo.net> sub 2048R/62E3DF34 2019-01-19 <<-------------------------- make sure there is a 'sub' line too. pub 2048R/C7A7F8E4 2018-12-30 uid OpenPGP signature key for the architect (created on 30th Dec 2018) <architect@matrix.com>
| 14. | If you do not have a key pair yet, use the command gpg --gen-key to create one. |
| 15. | Enter a name and an email address for the key pair creation. |
We tested the key pair generation with 'RSA and RSA' keys and 2048-bit keys.
When requested, enter a passphrase. This passphrase is used only on your local computer to keep the private key safe on your disk.
| 16. | gpg produces a pub/uid/sub text block identical to that of --list-keys output. |
| 17. | Use gpg -a --export THE_KEY_ID > FILENAME.asc to isolate the desired key. |
For example, in the example, use gpg -a --export F2061AC8 > PicoloDev.asc
The Picolo.net HD1 server preferably uses e-mail addresses to identify key owners.
You can identify a key without an associated e-mail address only through its hexadecimal signature.
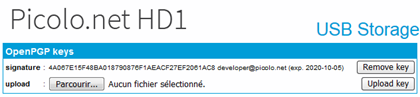
| 18. | Open the Storage page on your Picolo.net HD1. |
| 19. | Click on the Browse... button to select your exported .asc (or .pgp or .gpg) file. |
| 20. | Click on the Upload key button to add the key to the persistent configuration of the Picolo.net HD1. |
| 21. | Check that the hexadecimal string listed on the Picolo.net HD1 storage page matches the fingerprint of your key. |
To find your key fingerprint in Kleopatra, right-click the key in the main window and select Details in the contextual menu.
| 22. | Reboot your Picolo.net HD1 to generate and encrypt a passphrase with that key. |
Your Picolo.net HD1 now generates encrypted recordings:
| □ | The secure-<run-identifier>- prefix in the file names and the ready-GPG-AES-128 status in the Media Control panel of the Storage web page confirm the encryption. |
| □ | All recorded files are encrypted until you remove all the OpenPGP keys uploaded on the device. |
| □ | The keys are only valid until their expiry date. When a Picolo.net HD1 in OpenPGP+AES mode finds only expired keys, it does not start new recordings. |
